Kgb spy no longer sends logs. Spyware rating. Full multi-user support
KGB SPY is one of the most popular programs designed to spy on users personal computers. For this purpose, the KGB spy must be installed on the PC by some other user who has administrator rights on this machine.
This software allows you, unnoticed by a not very experienced user, to send email reports on the results of all his actions on specified address(usually this is mailing address the one who installed it). Discover this software product in the usual ways– not easy (if the one who installed it used the “hide” mode). The antivirus does not respond to this utility (especially if it is included in the exceptions), among the list installed programs it is not there; if you open C:\Program Files, it will be missing (or hidden).
Thus, when you begin to suspect that you are being followed, and you have an idea that this is being done using KGB SPY, you need to:
1. Detect whether the program is actually installed on the computer. This method is suitable when the spyware is installed by default. Select a key combination and press SHIFT+ALT+CTRL+K. The KGB Spy monitoring window will open. If nothing happens, there may be 2 options: this utility is not installed on the machine, or the keys quick access someone changed it.
2. Next method will also only work if the software was installed by default. Click on the “START” -> “RUN” button (or “START” -> “ALL PROGRAMS” -> “STANDARD” -> “COMMAND LINE”) and write “run kgb” in the line, and then press “ENTER” on the keyboard " The KGB SPY utility monitoring window will open.
3. How to remove kgb spy. This method suitable when the software product was installed by default. Open the task manager by pressing the key combination “Ctrl+Alt+Del” and then go to the “Processes” tab, then try to find the MPK.exe process there, end it, that’s it, the utility is turned off until the operating system is rebooted.
4. The following method also works when the default installation directory was not changed during installation. Install on your computer file manager, For example, Total Commander. Let's download it. Making everything visible hidden files by clicking: Configuration -> Settings -> Screen (Contents of panels) -> show hidden or system files. When using the default settings, KGB SPY is installed in the C:\Program Files folder. After going there, look for the “KGB” folder. Go to it and run the file “unins000.exe”. And that's it, the program is deleted.
5. You can also try to find the executive file called “unins000.exe” (KGB SPY is responsible for removing the utility), using the search function of Explorer, or using the search function of “Total Commander”, launch it and the spyware will be removed. Before starting, make sure that the file “unins000.exe” is in the required folder.
6. You can also search for the KGB folder using search (Explorer or Total Commander), and then open it and run “unins000.exe”.
And at the very end:
We prohibit all MPK.exe processes in the firewall, as well as any activity in the folder where the KGB spy was installed!!!
Personal Monitor
YOUR CHOICE
For parental controls
Discount for those who remember. On the checkout page, use coupon KGBSPY and get 70% off!
ATTENTION! The program is now called Mipko Personal Monitor!
Today it is almost impossible to find a computer that only one person has access to. Moreover, this applies not only to office, educational machines, etc., but also to the most common home PCs. After all, the whole family uses them. Of course, spying on your wife/husband is probably not very ethical. However, in some cases this is acceptable, for example, when your significant other is addicted to traveling to dubious sites, thereby jeopardizing the security of the PC. But there are still children.
Protection for your child
personal monitor for windows
Free version
for 3 days
Today, schoolchildren often surpass their parents in computer literacy. And therefore, it is quite difficult to control their work with the PC, and even more so to limit it. Meanwhile, sometimes it is simply necessary. How else will parents be able to find out what exactly their child was doing at the computer during the day: conscientiously writing an essay, reading jokes on the World Wide Web, or playing? The same question probably worries company leaders. What do employees do when their actions cannot be controlled? Are reports and contracts valid? The KGB Spy program will help you find the answer to all such questions and dispel any last doubts.
Very interesting program, I started using KGB Spy. Useful to use and necessary both at work and outside of it.
At its core, the KGB Spy program is keylogger. It intercepts and saves a detailed log of user actions on the hard drive, takes screenshots, records the launch of various software etc. Therefore, when installing and using it, the antivirus installed on your PC may issue a corresponding warning. However, there is no need to be afraid of this. In reality, KGB Spy is not malicious software and does not steal information. However, just in case, the user can prevent this utility from accessing the Internet, allowing it only to collect data (by appropriately configuring the PC security system). In this case, he can be confident in the security of his passwords, etc. confidential information. The main feature of the KGB Spy program, which immediately catches your eye when you first launch it, is that it is extremely simple and very user-friendly interface.
Almost all work with this utility is carried out in one window, divided into two parts. On the left there are links to access the information collected by the program and all the settings for the monitoring process. All of them are grouped in the form of a tree, which provides convenient access to any section the user needs. The right side of the window is used directly to view logs and configure monitoring. In addition, a detailed hint is displayed directly in it while setting parameters. This solution looks quite successful, since it greatly facilitates the development of the program. And finally, it is worth noting that the KGB Spy interface is multilingual: the user can independently select English, German or Russian.>
Now we can move on to consider functionality KGB Spy. And we will start, of course, with what types of monitoring are implemented in this program. There are six of them in total, and each of them can be turned on and off independently of the others. The first is the registration of user keystrokes. Moreover, the program can also record the use function keys(F1-F12, all possible combinations with the Alt and Ctrl buttons). In addition, in addition to the clicks themselves, the logs record their time, the program in which they were made, and the title of the active window. All this allows you to find out not only what exactly the user entered, but also in what software, in what open file he did it. The second type of monitoring is taking screenshots of the screen. They are necessary in order to clearly see what the user was doing in the absence of the PC owner. The program can take screenshots either on a timer (after a certain number of minutes) or when opening each new window. In addition, the administrator can specify what kind of pictures he needs (the entire screen or just the active window) and what quality they should be.
The next type of monitoring that KGB Spy can perform is monitoring software activity. When using it, the utility in question will save all running and closed software in the log. Thus, the PC owner will always know what programs were used in his absence. The fourth type of monitoring is tracking what information was saved to the clipboard.
Go ahead. The fifth type of information that the utility in question can save in logs is the addresses of visited web pages. This is very important because control over Internet use is very important. Visiting some sites can not only distract employees from work and affect the child’s psyche, but also seriously threaten the security of the computer. Therefore, control in this area is simply necessary. And finally, the last type of monitoring allows you to track the processes of turning on, shutting down and rebooting your computer. An important feature of the KGB Spy program is the hidden function, when activated, you can detect the utility using standard means OS is impossible. Moreover, interestingly, the user can either enable or disable it. In the first case, surveillance will be carried out secretly. And in the second, users will know that the PC owner controls their actions. This will be fair to them and will prevent attempts to misuse the computer. However, it is necessary to understand that visible work only makes sense if access to the settings of the program in question and the logs it saves is limited using built-in password protection.
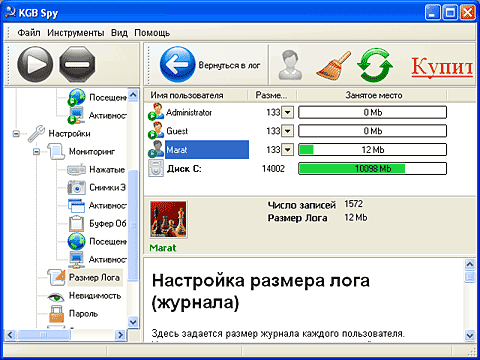
Another interesting opportunity KGB Spy's product is selective monitoring. Firstly, the computer owner can enable or disable for each user different kinds control up to the complete refusal to monitor the actions of some people. This approach allows you to flexibly configure the control system and minimize the size of recorded logs. This function can be very useful, for example, at home. Parents can create special accounts for their children (which, in fact, is normal practice) and include only them in monitoring. Secondly, the KGB Spy program allows you to specify a list of software that will be monitored or, conversely, will not be monitored. Using this feature will help reduce the size of logs without reducing their information content.

By the way, the size of the logs that KGB Spy saves can be controlled. The PC owner has the opportunity to set the maximum log size for each user and enable automatic removal information if the limit is reached. This prevents overflow hard drive and slowdown of the computer due to excessively large logs of the utility in question.
One more useful function implemented in the KGB Spy program is the possibility of remote control. To use it, the user must configure it: set access parameters to the FTP server or enter his email address. After this, the utility in question will independently send the collected information at a set time interval. Moreover, the PC owner has the opportunity to choose the type of this report (in HTML format or in the form ZIP archive), as well as the data that will be included in it (for example, everything except screenshots, only pressed buttons, etc.). The emergency alarm system deserves special mention. The essence of this function is as follows. First, the PC owner must specify a list of unwanted words. In the future, if the controlled user enters any of them, to the specified in the settings email A corresponding notification and, if necessary, a saved log will be sent immediately. , prevent leakage of confidential information, etc.

We also cannot help but talk about viewing the information collected by the KGB Spy program. We need to start with the fact that data can be presented in two forms. The first one is a table. In it, the computer owner can quickly view all records and their main characteristics: time, window title, event type, etc. (each type of monitoring has its own set of characteristics). For its convenience, the utility in question has the ability to sort the list by any field, as well as use filters (for example, view keys pressed only in Internet browser Explorer). The second type of information presentation is a report. It is intended for printing out collected information, for example for presenting it as evidence incorrect operation employee. Additionally, in the log viewing section there is a time filter, thanks to which you can view only unread entries or entries made in an arbitrary period of time. This is very convenient, since during active work the logs can reach significant sizes.
Spy KGB Spy allows you to set an invisible operating mode, so that no one will even guess that a real keylogger is monitoring it. KGB Spy quietly monitors the operation of the computer: records information entered from the keyboard, data from the clipboard, monitors visited sites.

How to detect and remove KGB Spy.
How to protect your personal information using Mask S.W.B from one of the most popular keyloggers - KGB Spy.
How computer user who does not have knowledge in the field information security, detect a spy hidden in your system, and protect yourself from surveillance without removing the keylogger from your computer in order to mislead the one who is spying on you? And how to remove the spy KGB Spy if you decide to do this? Let's consider the situation using the example of a common keylogger KGB spy and programs Mask S.W.B, which creates a secure platform for the user.
After launching Mask S.W.B antispyware, click the “System processes” button.

In the system processes window you can see everything running processes, except hidden ones.
To see if you have programs on your computer that are hiding themselves, click the “Hidden Processes” button.

In the hidden processes window, scroll the slider to the very bottom. All hiding programs (rootkits) will be highlighted in red.

In the picture above we see a spy program called KGB spy. This keylogger is configured to hide its actions and monitor the user.
If you want to remove Kgb Spy, select “Open application folder” from the context menu.

In the window that opens, run the uninstallation of the program and the spy will be removed.

If you just want to hide your actions from the keylogger and thereby mislead the one who is watching you, then enter the platform by clicking the button with the name of the program, as shown in the figure above.
Inside the protection platform, those programs that hide themselves from the user (rootkits) can be seen simply in the process window.

Program Mask S.W.B creates a safe environment in which you can do everything, but user behavior becomes uncontrollable for spyware.

Spies will not be able to see your actions performed on a protected platform, which means they will also not be able to transmit information about them to their owners. Mask S.W.B protects against recording video from the monitor screen, against taking screenshots, and does not allow receiving data from the keyboard and clipboard. In addition, it hides the websites you have visited and other information about your activities.
If you find a spy that your wife or your husband (or your boss at work) assigned to you, do not rush to remove it. Think: perhaps it is better for them to think that you are not doing anything unknown to them on the computer, since the spy will be clean. In the meantime, you can on the platform Mask S.W.B do whatever you want.
In the picture below we see that the KGB spy, after performing actions in the Mask S.W.B camouflage platform, was unable to record anything.

The masking program hides the user's actions from all existing this moment spies. With its help, you can detect and destroy computer spies that work at the level of system kernel drivers and are invisible to antivirus programs.
Download the anti-spyware program Mask S.W.B and check whether you are being monitored using KGB spyToday it is almost impossible to find a computer that only one person has access to. Moreover, this applies not only to office, educational machines, etc., but also to the most common home PCs. After all, the whole family uses them. Of course, spying on your wife/husband is probably not very ethical. However, in some cases this is acceptable, for example, when your significant other is addicted to traveling to dubious sites, thereby jeopardizing the security of the PC. But there are still children. Today, schoolchildren often surpass their parents in computer literacy. And therefore, it is quite difficult to control their work with the PC, and even more so to limit it. Meanwhile, sometimes it is simply necessary. How else will parents be able to find out what exactly their child was doing at the computer during the day: conscientiously writing an essay, reading jokes on the World Wide Web, or playing? The same question probably worries company leaders. What do employees do when their actions cannot be controlled? Are reports and contracts valid? The KGB Spy program will help you find the answer to all such questions and dispel any last doubts.
At its core, KGB Spy is a keylogger. It intercepts and stores on the hard drive a detailed log of user actions, takes screenshots, records the launch of various software, etc. Therefore, when installing and using it, the antivirus installed on the PC may issue a corresponding warning. However, there is no need to be afraid of this. In reality, KGB Spy is not malicious software and does not steal information. However, just in case, the user can prevent this utility from accessing the Internet, allowing it only to collect data (by appropriately configuring the PC security system). In this case, he can be confident in the security of his passwords and other confidential information.
The main feature of the KGB Spy program, which immediately catches your eye when you first launch it, is its extremely simple and very convenient interface. Almost all work with this utility is carried out in one window, divided into two parts. On the left there are links to access the information collected by the program and all the settings for the monitoring process. All of them are grouped in the form of a tree, which provides convenient access to any section the user needs. The right side of the window is used directly to view logs and configure monitoring. In addition, a detailed hint is displayed directly in it while setting parameters. This solution looks quite successful, since it greatly facilitates the development of the program. And finally, it is worth noting that the KGB Spy interface is multilingual: the user can independently select English, German or Russian.
Now we can move on to reviewing the functionality of KGB Spy. And we will start, of course, with what types of monitoring are implemented in this program. There are six of them in total, and each of them can be turned on and off independently of the others. The first is the registration of user keystrokes. Moreover, the program can also record the use of function keys (F1-F12, all kinds of combinations with the Alt and Ctrl buttons). In addition, in addition to the clicks themselves, the logs record their time, the program in which they were made, and the title of the active window. All this allows you to find out not only what exactly the user entered, but also in what software, in what open file he did it.
The second type of monitoring is taking screenshots of the screen. They are necessary in order to clearly see what the user was doing in the absence of the PC owner. The program can take screenshots either on a timer (after a certain number of minutes) or when opening each new window. In addition, the administrator can specify what kind of pictures he needs (the entire screen or just the active window) and what quality they should be.
The next type of monitoring that KGB Spy can perform is monitoring software activity. When using it, the utility in question will save all running and closed software in the log. Thus, the PC owner will always know what programs were used in his absence. The fourth type of monitoring is tracking what information was saved to the clipboard. 
Go ahead. The fifth type of information that the utility in question can save in logs is the addresses of visited web pages. This is very important because control over Internet use is very important. Visiting some sites can not only distract employees from work and affect the child’s psyche, but also seriously threaten the security of the computer. Therefore, control in this area is simply necessary. And finally, the last type of monitoring allows you to track the processes of turning on, shutting down and rebooting your computer.
An important feature of the KGB Spy program is its hidden function, when activated, it is impossible to detect the utility using standard OS tools. Moreover, interestingly, the user can either enable or disable it. In the first case, surveillance will be carried out secretly. And in the second, users will know that the PC owner controls their actions. This will be fair to them and will prevent attempts to misuse the computer. However, it is necessary to understand that visible work only makes sense if access to the settings of the program in question and the logs it saves is limited using built-in password protection.
Another interesting feature of the KGB Spy product is selective monitoring. Firstly, the computer owner can enable or disable various types of control for each user, up to a complete refusal to monitor the actions of some people. This approach allows you to flexibly configure the control system and minimize the size of recorded logs. This function can be very useful, for example, at home. Parents can create special accounts for their children (which, in fact, is normal practice) and include only them in monitoring. Secondly, the KGB Spy program allows you to specify a list of software that will be monitored or, conversely, will not be monitored. Using this feature will help reduce the size of logs without reducing their information content. 
By the way, the size of the logs that KGB Spy saves can be controlled. The PC owner has the opportunity to set the maximum log size for each user and enable automatic deletion of information if the limit is reached. This allows you to prevent your hard drive from filling up and your computer from slowing down due to excessively large logs of the utility in question.
Another useful feature implemented in the KGB Spy program is the possibility of remote control. To use it, the user must configure it: set access parameters to the FTP server or enter his email address. After this, the utility in question will independently send the collected information at a set time interval. Moreover, the PC owner has the opportunity to choose the type of this report (in HTML format or as a ZIP archive), as well as the data that will be included in it (for example, everything except screenshots, only pressed buttons, etc.).
The emergency alarm system deserves special mention. The essence of this function is as follows. First, the PC owner must specify a list of unwanted words. In the future, if a controlled user enters any of them, a corresponding notification and, if necessary, a saved log will be immediately sent to the email specified in the settings. This can help parents protect their children from unpleasant situations, prevent leakage of confidential information, etc. 
We also cannot help but talk about viewing the information collected by the KGB Spy program. We need to start with the fact that data can be presented in two forms. The first one is a table. In it, the computer owner can quickly view all records and their main characteristics: time, window title, event type, etc. (each type of monitoring has its own set of characteristics). For its convenience, the utility in question has the ability to sort the list by any field, as well as use filters (for example, view keys pressed only in the browser Internet Explorer). The second type of information presentation is a report. It is designed to print out collected information, for example to present it as evidence of incorrect employee performance. Additionally, in the log viewing section there is a time filter, thanks to which you can view only unread entries or entries made in an arbitrary period of time. This is very convenient, since during active work the logs can reach significant sizes.
Well, now all that remains is to summarize. The KGB Spy product is a real spy that monitors the work of users. But this spy, unlike malware, is useful. Of course, its use is not always ethical. However, in many cases the use of such tools is not only justified, but also necessary.
KGB Archiver is a free computer archiver created by Tomasz Pawlak. It is a graphical shell for the author's modification of the PAQ1-7 compression algorithm.
KGB Archiver uses one of the most reliable AES-256 algorithms to encrypt archives. At the same time, it should be noted that there are increased requirements for computer hardware, especially the number of random access memory. Depending on the compression level, from 9 MB to 1.6 GB of RAM is required. The archiver also supports its own KGB format, as well as ZIP.
There is a version for operating systems Microsoft Windows and a console beta version for POSIX systems.
Key features and functionality of KGB Archiver
- Support for archives with ZIP and KGB formats.
- Creating self-extracting archives.
- Encryption using 256-bit AES key.
Tests show that the compression ratio of KGB Archiver is not much higher than that of the popular RAR and Cab archivers; the packaging and, most critically, unpacking times are orders of magnitude longer. The actual requirements for the size of RAM are also large.
Disadvantages of KGB Archiver
- Using the .kgb extension for archives (which is already used by Mercury Development's Kremlin Encrypt) leads to a conflict.
- In versions 1.x, incorrect creation of ZIP archives from a small (less than 1 kilobyte) file was noticed.
The archiving result could not be unpacked.
- The list of files is not archived, so if there are a large number of small files, the compression level drops sharply.
- Supports only .KGB and .ZIP formats.