How can I read an Agent's story? How to read a story in a mail agent
The program "Mail.ru Agent", which many people use for instant messaging, by default stores the entire history of correspondence on the hard disk of the computer on which it is installed. If you have forgotten your password and cannot open the program, you can access the dialog history using additional software tools.
Instructions
Good Sunday evening, dear reader! Before you material, all information in which is based on my personal experiments and rich experience. In today's article, you will learn how the interception of [email protected] is taking place. After all, many malefactors can learn how to read someone else's [email protected]. It is important to be able to protect your information from unauthorized hacking! You will find a useful video at the end of the article.
Why did it become necessary to deal with such questions? How to read someone else's [email protected] and intercept it without knowing the user's password? I just needed a convenient program for quick messaging with colleagues at work, relatives, friends. Nothing more universal could be found. I have been using this messenger for several years now. But doubts were always tormented, but does someone read my messages? To hack someone else's correspondence [email protected], you would need some specialized applications. So I went to the Internet in search of them.
In any search engine, upon the request "how to look at someone else's [email protected]", you will see a colossal number of different links. On verification, it turns out that 99% of them are scams, viruses, and other malware. Yes, there were some that were launched, but they did not work. I performed all tests on my smartphone running Android 4.1. Nothing with remote access was found - such are the disappointing conclusions! Do not fall for the empty promises of malefactors!
And yet, I thought about how to view and intercept someone else's [email protected] with more familiar applications. For example, utility utilities for backing up information! Initially, Android does not have them, but it will not be difficult to pick up and download them. There are hundreds of similar programs even in the Play Market. But the problem lies in the fact that there are not enough functions in them. I reviewed many applications until I finally came across a great service. He does not know how to hack and intercept other people's correspondence [email protected], and he was not created for this.
The essence of the service is as follows: a standard program of the .apk format is installed on an Android mobile phone, which collects information and sends it to a personal user account. This is a special section where data is stored for 30 days. It is very convenient to view them there. You will find the account on a separate website, so unauthorized persons will not get access there. Only the person who installed and configured the utility.
But imagine a situation in which an attacker will try to intercept and read someone else's [email protected]! He may try to install a similar program on your phone! And it doesn't matter which one. To prevent this from happening, try not to throw your mobile phone anywhere, do not leave it unattended, do not pass it into unfamiliar hands. And also people you don't trust 100%!
Next, there will be a video on Youtube, recorded by me for the readers of this blog. It describes the process of installing and configuring the utility, which I wrote about above. Convenient backup options will open before you! But such utilities cannot be installed in other people's phones! The owner of a mobile phone will definitely not like it if his personal information begins to be sent to someone who is not clear.
Application features: reading correspondence SMS, MMS, Vkontakte (official application and Kate Mobile), Odnoklassniki, Facebook, Moi [email protected], Vseti.by, Twitter, Hangouts, Google+, WhatsApp, Skype, Viber, Hangouts (formerly Google Talk ), [email protected], ICQ, IM + and IM + Pro, AIM, Jabber, MSN, MySpace, Yahoo! and Ya.Online (Yandex Chat), Email correspondence Gmail and [email protected], view visited sites in browsers Chrome, Opera, Firefox. Get access to the list of calls and the location of the phone. This is a small part of all the possibilities. The whole
Video installation guide for any phone:
Video guide for installing on a phone with ROOT rights:
Installation and configuration instructions:
- We start a personal account using this link: "Create a personal account" (just register there).
- Go to this link: "Enter your personal account on the site" and enter the Email and password that you specified before registration.
- We press the button: "Add phone"
- We fill in all the fields that are asked to enter. We fill it in correctly as it is written there, otherwise it will not work.
- Click the "Save" button.
- We read the instructions that appeared after clicking the "Save" button
- We install the application on the phone (the one from which you need to get information), and configure it according to the instructions that you will have to read in step 6.
- The application is installed. Things are good. The developers write that you need to wait at least an hour for the data to start flowing into your personal account that you entered in step 1. In our case, the data came in 4 hours. The plan succeeded! Wish you success.
You hardly use Mail.Ru Agent, but this is a wildly popular service that is gaining momentum every day. According to official figures, the monthly audience of this messenger at the end of last year was an insane figure of 21.4 million people. It's easy to explain - the product is really successful. But today I want to talk about how the file with the user's message history was parsed.
WARNING
Do not forget about Article 138 - "Violation of the secrecy of correspondence, telephone conversations, postal, telegraphic or other messages" of the Criminal Code of the Russian Federation, as well as the presence in it of Chapter 28 - "Crimes in the field of computer information" (Articles 272, 273, 274).
Hack history
The experiment began for me back in 2008, when a friend asked me to check the correspondence of his girlfriend in Mail.ru Agent. Then the history file was a simple textbook with the name email history.txt and had a primitive structure compared to mra.dbs (the file that currently stores the history of correspondence and contact data). In a couple of hours, a simple but effective RTF converter was written, which did all the dirty work of pulling correspondence from the Agent. The friend was delighted. Further, in the course of studying programming in compiled languages, as a practice I wrote the Mail.ru History Reader program, the description of which got on the pages] [in August 2009. Having received a large number of positive reviews, I published the structure of the format of the then history file (see links in the side offset) and the source code of the reader. However, Mail.ru Agent continued to evolve, and a new advanced mra.dbs file took over. After this event, I received tons of messages from various people asking me to take care of it. In the company with SOLON7, we poked around this file in the HEX editor, trying to find structures, references to offsets and all kinds of changes after the launch of the Mail.ru Agent. By the end of 2010, after a long search, the format finally conquered.
Rich Text Format (RTF)
RTF, used in mra.dbs, is a format for storing markup documents, proposed back in 1982 by bearded programmers from Microsoft and Adobe. To parse it, it is not at all necessary to reinvent the wheel, but just send the EM_STREAMIN message with the SF_RTF flag for writing and EM_STREAMOUT with the SF_TEXT flag for reading:
EDITSTREAM es = (0); es.pfnCallback = EditStreamCallback; es.dwCookie = (DWORD_PTR) SendMessage (hRich, EM_STREAMIN, SF_RTF, (LPARAM) & es);
This simple trick is used in my reading room.
How do I get the mra.dbs file?
You, of course, ask yourself a question: where, in fact, is this notorious mra.dbs stored, and how to get it? The mra.dbs file is stored in the "% APPDATA% \ Mra \ Base \ mra.dbs" folder (for example, "C: \ Documents and Settings \ user \ Application Data \ Mra \ Base \ mra.dbs"), and get it when the The agent is not so difficult, it is enough just to use the ExpandEnvironmentStrings and CopyFile functions. However, when the Agent is enabled, the mra.dbs file is busy and the system will simply not allow using it. To solve this problem, you can, for example, temporarily disable the Agent (for this action you will need debugger privileges, which can only be obtained with Administrator rights) or find the open file handle in the system, and then duplicate it into the address space of your process. You can also read a file directly from disk (though you need to know what a cluster is and how to work directly with a file system driver) or write your own file driver (this is almost impossible). Everything would be fine, but in practice, all of the above methods have their drawbacks. When enumerating handles using ZwQuerySystemInformation and copying them to your process using DuplicateHandle, you can face two problems. The first is that when ZwQueryInformationFile is called, the thread may hang, waiting for a response from the blocking named pipe. The second - after copying, both handles (ours and the process that opened the file) will point to one FileObject, and therefore the current I / O mode. The position in the file and other information related to the file will be shared between the two processes, so even reading the file will cause the reading position to change and disrupt the normal operation of the program that opened the file. Of course, you can suspend all threads of the file process for a while, and after copying, restore read positions and start the owner process again, but this is time-consuming and expensive. It would seem that direct reading from disk may be the ideal method, but there are also disadvantages here. In this way, you can only read files that are opened with FILE_READ_ATTRIBUTES access (except for swap files), the file must be uncompressed, not encrypted (otherwise we will read nonsense) and have its own cluster (small files in NTFS can be entirely located in MFT). It should also be taken into account that during reading the file can be changed (and we will get unclear what as a result). Therefore, we will analyze the simplest method with temporarily disabling the Agent process.
So, in order to kill the Mail.ru Agent process, first you need to find out its identifier (ProcessID). This can be done in different ways: through the ToolHelp API, through the Native API (using the ZwQuerySystemInformation function), by traversing the list of open handles, or by the list of windows opened by the process (GetWindowThreadProcessId). The easiest option is to use the ToolHelp API and search by the name of the exe file. To do this, just call the CreateToolhelp32Snapshot> Process32First> Process32Next functions, and then in the loop body check the value of the szExeFile field of the PROCESSENTRY32 structure with magent.exe. The ProcessID we need is in the same structure, the th32ProcessID field:
HProcessSnap = CreateToolhelp32Snapshot (TH32CS_SNAPPROCESS, 0); if (INVALID_HANDLE_VALUE! = hProcessSnap) (pe32.dwSize = sizeof (PROCESSENTRY32); if (Process32First (hProcessSnap, & pe32)) (do (if (0 == lstrcmp (pe32.szExeFile, _TEXT ("magent.exe"))) (pid = pe32.th32ProcessID; break;)) while (Process32Next (hProcessSnap, & pe32));) CloseHandle (hProcessSnap);)
After we find the PID, we need to get the privileges of the SeDebugPrivilege debugger (OpenProcessToken> LookupPrivilegeValue> AdjustTokenPrivileges) and kill the process (OpenProcess> TerminateProcess), and then try to call CopyFile again. Privileges can also be obtained in a more elegant way - through the Native API:
Void GetPrivilege (IN ULONG Privilege) (BOOLEAN OldValue; RtlAdjustPrivilege (Privilege, TRUE, FALSE, & OldValue);)
Everything, mra.dbs is in our hands. Now let's move on to gutting it :).
Revealing the secrets of mra.dbs
The mra.dbs file is a memory dump of the Mail.ru Agent, so it is not possible to open it for reading while the program is running (for an ordinary programmer, but we have our own secrets :), the task is also complicated by the fact that all numbers are stored in memory upside down. However, let's dive a little deeper into reverse engineering.
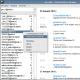
So, in the depths of mra.dbs there is a hash table that describes offsets by 4-byte identifiers. The identifiers are used to determine the beginning of the recording of various structures and dump segments, among which are the correspondence history records we need (pay attention to the corresponding illustration):
Typedef struct _ids (unsigned int id1; unsigned int id2; unsigned int count;) _ids;
INFO
A hash table is a data structure that implements an associative array interface, it allows you to store key-value pairs. A doubly linked list consists of data items, each of which contains links to both the next and the previous item.
The beginning of the story is characterized by the mrahistory_ keyword, followed by the e-mail of the owner of the mra.dbs file and the e-mail of the contact with whom the correspondence is being conducted. In the case of history, the identifiers form a doubly linked list: the first leads to the first message sent, and the second to the last received message. The number of messages can be found by examining the four bytes after the identifiers (structure _ids). After going through the offset of the identifier (it can be found out from the hash table), we will get to the message record (again, all attention to the corresponding figure):
Search hash table struct _message (unsigned int size; unsigned int prev_id; unsigned int next_id; unsigned int xz1; FILETIME time; unsigned int type_mesage; char flag_incoming; char byte; unsigned int count_nick; unsigned int magic_num; // 0x38 unsigned int count_message ; unsigned int xz2; unsigned int size_lps_rtf; unsigned int xz3;);Dump lines are saved in Unicode (wchar_t) in various ways:
- with a terminating null at the end of the line;
- in the LPS structure (the name of the structure is taken from the description of the MMP protocol format), where the first four bytes indicate the length of the following line;
- in RTF format.
Knowing the number of messages, it will not be difficult for us to go through the entire chain. But how do you even know where this hash table is, and how do you find the beginning of the history records? SOLON7 and I spent many sleepless nights searching for answers to these questions.
Mra.dbs message types
- 2 - unauthorized users;
- 4 - authorization requests;
- 7 - regular messages;
- 10 - file transfer;
- 35 - microblog entries;
- 46 - change of geolocation.
A bit of magic
At offset 0x10 from the beginning of the mra.dbs file, as it turned out, the address of the cherished hash table is stored. Traversing the offset of the first index from the hash table, we come across the initial data structure. Perhaps there is generally all the information contained in mra.dbs. Move on. At offset 0x20, this structure stores the number of history records or, more simply, the number of correspondences. Since the dump file is constantly expanding, the ID of the last recorded history is located at offset 0x2C - this is all we need to know in order to start looking for correspondence IDs. In general, the algorithm is as follows:
- we go through the identifiers of the history records using a loop (starting from the last added record);
- if the word "mrahistory_" is present in this record from offset 0x190, it means that at offset 0x24 there are message chain identifiers of this correspondence.
To make it a little clearer, take a look at this code:
DWORD * offset_table = (DWORD *) (mra_base + * (DWORD *) (mra_base + 0x10)); DWORD end_id_mail = * (DWORD *) (mra_base + 0x20 + offset_table); DWORD count_emails = * (DWORD *) (mra_base + 0x2C + offset_table); ... for (int i = 0; i 
Code
Now I will show you only the most basic points. So, the mra.dbs file is a memory dump, so we will not pervert and use functions to work with file offsets, but we will immediately place it in the memory of our program. To do this, we use the resources of the Windows OS and create a Memory Mapped file:
CreateFile CreateFileMap MapViewOfFile VirtualFree CloseHandle CloseHandle
Since we do not need to save the changes made back to the file, VirtualFree is used here instead of UnmapViewOfFile. The first thing we will do is find all the contacts from the chat history. We will store the found goodness in the emails structure:
Typedef struct _emails (wchar_t * email; _ids * id;); ... struct _emails * emails; ... emails = VirtualAlloc (NULL, count_emails * sizeof (struct _emails), ..); ...
After traversing the identifiers and searching for the "mrahistory_" string, our structure will be filled with identifier addresses. Note that we did not copy even a byte and used only 16 * count_emails bytes (for example, with 1,000 contacts, we use only ~ 15 kilobytes of memory). Now, having in hand the identifiers of the beginning of the correspondence with a specific user, we can read the messages:
Int id_message = emails [k] .id-> id1; for (int i = 0; i
The message date is stored in FILETIME format and can be converted to human readable form for convenience using the FileTimeToSystemTime function. The RTF format is perfectly accepted by Rich Edit and any other standard editors such as WordPad. But you don't have to bother with this, since messages are stored unformatted immediately after the nickname, and their size is specified in the message structure. That's all you need to know to get a digestible list of messages from the Agent.
P.S.
Unfortunately, the format of the magazine does not allow me to present my hardcore research in full here, so hurry to take a look at the disc. I hope that the example of the reader code (the exe's of which, by the way, with the help of a small optimization, fit only 2 kilobytes without any packers) will help you in writing fast and cool C code, as well as in learning hex editors and other low-level things. By the way, the equally fascinating topic of reading the history of ICQ correspondence, which is also stored in the mra.dbs file, remained unaffected. Thanks to Mail.Ru, firstly, for the development of the Mail.Ru Agent, secondly, for the noticeable development of your favorite ICQ, and thirdly, for the interesting quest that I told you about today.